According to Wikipedia (https://en.wikipedia.org/wiki/Phishing) Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly,money), often for malicious reasons, by masquerading as a trustworthy entity in an electronic communication
This case is not about Phishing, because this campaign doesn't try to achieve sensitive information, but instead of phishing it is "something else"...
This email has been delivered in one of my mailbox honeypots.
It's very easy to understand that it is a fake email, but even if today the most of the people believe that it is authentic. This is due the fraudster's evil idea to hits the most sensitive part of the mind of every person, the pocket and the money.
This email seems to come from the Italian Agency that praise taxes.
Clicking on the hyperlink "Scarica il Documento", a web page will be showed to the end user.
Here a file named "Documento Numero 00020160830.pdf" will be download.
At the first time I didn't pay attention to the phrase "La password per accedere alla fattura è 7604", and I have focused my attention on the file.
I decided to open the document. The icon was a zip icon but by enabling the folder's option "show file extension", the extension was ".pdf".
Well, as I expected it was a zip file, but it asked me a PASSWORD. I was reminded about the password printed in the webpage, I have put it and the file was extracted.
-------------------- STATIC ANALYSIS --------------------
The sample file was packed using NullSoft Software.
A packer is a special program used to obfuscate the entire file.
Investigating into the sample file, two digital certificates have been discovered.
One of this digital certificate has been revoked.
-------------------- CODE REVERSE ENGINEERING --------------------
The pictures below report a code snippet to show how the malware checks and asks the path of "Temp" directory
...and below is reported the request for "ResourceLocate" directory in order to achieve GUI language.

Into pictures reported below there are strings, like DLL file names, URL and Domain, but also part of command like "[Rename]\r\n"
-------------------- DYNAMIC ANALYSIS --------------------
Checking the performance graph is easy to note that only the process "xkpgcoc.exe" was doing I/O activity on disk."

At the end of its task, this was the result:
All data into my virtual environment was encrypted by CTB-Locker. The extension used to encrypt files has been seven random chars. The file name pattern after the encryption is:
<Original_File_Name>.<Original_Extension_Uppercase>.<Seven_Random_Chars>.
Running this ransomware more than one time, I noted that it changes every time the crypt-extension.
Killing the process"xkpgcoc.exe", the countdown disappear and we can read on desktop background the instructions to pay and recovery files. During the malware execution, no network traffic was generated. This mean that the cryptolocker doesn't comunicate with a C2C Server The public key are generated locally using a specific algorithm.
Instruction is also reported in a TXT file, named "!Decrypt-All-Files-aruugia.txt" and "!Decrypt-All-Files-aruugia.jpg", located within "Documents" directory.
Is useful to note four important things:
- The Cryptolocker didn't identify that it wasrunning on a Virtual environment
- The Cryptolocker didn't network connections with any C2C server
- The countdown was not TRUE
- There are not information about how much the user have to pay to recovery files.
Going one step ahead, Tor website has been checked, in order to understand the process that the user have to follow in to recovery files.
Typing the public key into the form, we receive the following webpage.
The payment simulation has been done different weeks after the infection. This demonstrate how the countdown is fake and it is useful only to scared the victim.
The webpage reported above could be reached directly knowing the URL. This mean that the fist page does not made a real check on the public key reported into the desktop background and into the instruction files.
The only check that the first web page do, is to verify if the key was generated by the algorithm embedded into the cryptolocker. A random Public Key does not works and an an error was reported to the user.
This is a trick to lure the user or a not expert analyst.
It is a CTB-Locker and there is no known way to decrypt files encrypted by it without paying the ransom. (as reported by Kaspersky)
Everyone of Kaspersky and TrendMicro decrypter was tested and no one of them have been able to decrypt the files encrypted with CTB-Locker.
-------------------- FORENSICS ANALYSIS --------------------
Below is reported the changes that this ransomware did into my VM.
----------------------------------
Chiave cancellata (removed keys) :3
----------------------------------
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{688d2436-fb66-11e5-8224-08d40c63bf18}\shell
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{688d2436-fb66-11e5-8224-08d40c63bf18}\shell\Autoplay
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{688d2436-fb66-11e5-8224-08d40c63bf18}\shell\Autoplay\DropTarget
----------------------------------
Chiave aggiunta (added keys):32
----------------------------------
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Logon\{9C691604-1C86-496F-9A97-388265B2C111}
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{9C691604-1C86-496F-9A97-388265B2C111}
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\bxymszh
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\PML
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aruugia
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.aruugia\OpenWithList
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.PML
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.PML\OpenWithList
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.PML\OpenWithProgids
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.PML
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows Photo Viewer
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows Photo Viewer\Viewer
...(continue)
----------------------------------
Valore cancellato (changed values) :3
----------------------------------
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{688d2436-fb66-11e5-8224-08d40c63bf18}\shell\: "None"
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{688d2436-fb66-11e5-8224-08d40c63bf18}\shell\Autoplay\MUIVerb: "@shell32.dll,-8507"
HKU\S-1-5-21-682910469-3081883402-3337175249-1000\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{688d2436-fb66-11e5-8224-08d40c63bf18}\shell\Autoplay\DropTarget\CLSID: "{F26A669A-BCBB-4E37-ABF9-7325DA15F931}"
----------------------------------
Valore aggiunto (added values) :134
----------------------------------
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{9C691604-1C86-496F-9A97-388265B2C111}\Path: "\bxymszh"
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{9C691604-1C86-496F-9A97-388265B2C111}\Hash: 9C B1 E8 C3 45 CA 30 48 28 22 AF C4 95 DE F4 83 97 E3 11 86 A1 0B 33 AC 0A C1 AF 69 13 65 02 8E
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{9C691604-1C86-496F-9A97-388265B2C111}\Triggers: 15 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 FF FF FF FF FF FF FF FF 58 21 41 00 48 48 48 48 93 EB 00 1F 48 48 48 48 00 48 48 48 48 48 48 48 00 48 48 48 48 48 48 48 01 00 00 00 48 48 48 48 1C 00 00 00 48 48 48 48 01 05 00 00 00 00 00 05 15 00 00 00 05 63 B4 28 0A CF B1 B7 D1 40 E9 C6 E8 03 00 00 48 48 48 48 28 00 00 00 48 48 48 48 57 00 49 00 4E 00 2D 00 50 00 35 00 44 00 49 00 46 00 51 00 42 00 30 00 43 00 31 00 47 00 5C 00 6D 00 61 00 63 00 00 00 38 00 00 00 48 48 48 48 58 02 00 00 10 0E 00 00 80 F4 03 00 FF FF FF FF 07 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 AA AA 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 FF FF FF FF FF FF FF FF 00 00 00 00 FF FF FF FF 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 01 00 69 00 63 00 65 00 3A 00 00 00 69 00 2E 00 00 48 48 48 48 48 48 48 00 48 48 48 48 48 48 48 01 00 00 00 48 48 48 48 1C 00 00 00 48 48 48 48 01 05 00 00 00 00 00 05 15 00 00 00 05 63 B4 28 0A CF B1 B7 D1 40 E9 C6 E8 03 00 00 48 48 48 48 28 00 00 00 48 48 48 48 57 00 49 00 4E 00 2D 00 50 00 35 00 44 00 49 00 46 00 51 00 42 00 30 00 43 00 31 00 47 00 5C 00 6D 00 61 00 63 00 00 00
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{9C691604-1C86-496F-9A97-388265B2C111}\DynamicInfo: 03 00 00 00 1A E5 82 A7 10 11 D2 01 1A E5 82 A7 10 11 D2 01 00 00 00 00 00 00 00 00
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\bxymszh\Id: "{9C691604-1C86-496F-9A97-388265B2C111}"
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\bxymszh\Index: 0x00000002
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32\EnableFileTracing: 0x00000000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32\EnableConsoleTracing: 0x00000000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32\FileTracingMask: 0xFFFF0000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32\ConsoleTracingMask: 0xFFFF0000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32\MaxFileSize: 0x00100000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASAPI32\FileDirectory: "%windir%\tracing"
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS\EnableFileTracing: 0x00000000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS\EnableConsoleTracing: 0x00000000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS\FileTracingMask: 0xFFFF0000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS\ConsoleTracingMask: 0xFFFF0000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS\MaxFileSize: 0x00100000
HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\xkpgcoc_RASMANCS\FileDirectory: "%windir%\tracing"
...(continue)
As I expected, into this folder there was a file named "bxymszh" without a file extension.
Note: Also this file name changes if the cryptolocker is executed more than one time restoring the VM snapshot.
The content of this file are reported below:
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo />
<Triggers>
<LogonTrigger id="Trigger1">
<Enabled>true</Enabled>
<UserId>mac</UserId>
</LogonTrigger>
</Triggers>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>true</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>false</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<Duration>PT10M</Duration>
<WaitTimeout>PT1H</WaitTimeout>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT72H</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\Users\%USER_NAME%\AppData\Local\Temp\xkpgcoc.exe</Command>
</Exec>
</Actions>
<Principals>
<Principal id="Author">
<UserId>HIDDEN_BY_ME</UserId>
<LogonType>InteractiveToken</LogonType>
<RunLevel>LeastPrivilege</RunLevel>
</Principal>
</Principals>
</Task>
Below is reported the Temp folder content that includes: 2 folders and one exe file that is the process that has been executed by the evil file ("Documento Numero 00020160830.pdf.exe").
Running this ransomware more than one time, exe file's name (xkpgcoc.exe) does not changes but folders name change every time.
The content of two folders "nsmFEF9.tmp" and "nsbEDF8.tmp" is a DLL file, named "System.dll".
Analyzing both DDLs, them seams to be identical, same strings, same function names (Store, Copy, Alloc), etc, but they are located in two different folders. I suppose an development mistake into the source code.
Going to the parent directory I found other files with not classic extensions.
This name of these file, contrary to the others DOESN'T change if the malware is executed more than one time.
We have some good IOCs :)

Going to the parent directory I found other files with not classic extensions.
This name of these file, contrary to the others DON'T change if the malware is executed more than one time.
We have some good IOCs :)
In brief, this Cryptolocker use the real CTB-Locker algorithm to encrypt files that until now has been not cracked. Anyway there is a gray area about it that want to summarize in some points:
- The end-user download a zipped file protect with password that is reported in a static webpage.
- The Onion web page located into the dark web with a bypass of the first screen.
- The countdown is only a fake.
- Two equals DLL files
Every of these points improved or decreased the fraudster's economy?...If the end-user after the file download removed the email? The fraudster has failed at the first step.
How much it's not worth the trouble?
This was a very strange campaign with a very sophisticated Cryptolocker but with some ordinary mistakes did by a not expert person.
IoCs
Into \AppData\Local\:
- aclfepwx.cb
- aom.t
- cwmlmn.p
- jbibns.sm
- jsrthsll.lj
- ljyg.wqbv
- pnvj.t
- rcdsn.uv
- rgfihvmy.uqmas.wp
- s.wp
- wb.ibkh
- x.am
- yjkjaryt.b
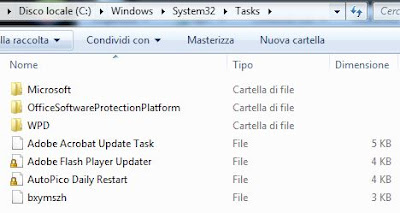
Into \System32\Tasks
- xkpgcoc.exe
MD5: 474e163b1da51a3da12290190e508f05
SHA1: 126e8fbd68dbf76e9e20477729555049cbe89dd8