I am here to tell about the "story of an image"...
Well, let's gooooooooo!!
Watching the picture below, what you can tel about it? Is it a simple image?
...and in the following picture?
YES!! They are the same picture, the first one is what you can see when you open it. The second one, is what you can see if you open it using for example a simple text editor.
Today I want to tell you about a malware that I discovered during my activity as researcher, malware hunter and malware Analyst.
It uses an image (JPG file) with embed a shellcode in order to infect the Linux System.
Shellcode Analysis:
Image reported above show part of image coded file and embedded shellcode in clear text.
Second line, command "crontab", is a time-based job scheduler in Unix-like computer operating systems.
"Crontab" option "-r" is present only in some Linux distro like Debian, Centos and Redhat. I can image that this malware is focused to Linux distro quoted above.
Third line of shellcode get seconds and transform them in days from 1970, then store them in a variable named"days".
Sum the value 983 to "days" variable and assign this value to variable named"days2".
Then "days" variable will have the first 10 elements of MD5's digest of "days2" .
Into shellcode's snippet reported below it is listing processes and concatenate other commands like xargs and awk.
The last one searches files that have text that match the pattern, when a line or text matches, awk performs a specific action on that line/text. In this case concatenating "print $2", it return the second item (proces' ID) and then kill it.
Using command "pkill -f", shellcode kills processes which matches the pattern for any part of the command line
This shellcode's snippet is used to kill any others miner that had infected the machine, in order to be the only one to use it.
"DoMiner" function using Curl command download into "tmp" folder a file image JPG named "car-498167.jpg" from website "imagehousing[dot]com" and rename this image with "days" variable's value.
Then skips the first 2931 byte and save it again.
After this task file's permission is changed with execution privileges and in the end it use "nohup" command line-utility which allows to run command/process or shell script that can continue running in the background after you logout from a shell.
Sleep and then remove everyone file with name "days" and "daybefore".
NOTE: No part of source code file named "daybefore.jpg" has been created. Only a variable was created using this name.
Why put this shellcode line? Are there typographical error?
Carry on downloading image file "car-498167.jpg" using browser. It looks like the first one.
A quick analysis shows that it doesn't contains evil shellcode or evil artifacts, but I discovered a very interesting information.
As you can read, it is packed with UPX packer, version 3.91.
I create a bash script in order execute it in debug mode, download image and skip 2931 byte as wrote into source code.
Below you can see my bash script and its result in terms of files.
Note: "12days" and "13days" are names that personally I decided to appoint to this images.
Above you can see both file, the first one (the image file) and the second one (executable file) that is the first one without 2931 bytes. Below you can take a look to the files size.
I used UPX packer to unpack ELF file. Below is reported a screenshot that contains details (format, compression ration, actual and future file size) about ELF executable file.
Now it's time to unpack ELF executable file
Below are reported details about ELF's file.
Shellcode In-depth Analysis:
Working on it and downloading "car-498167.jpg" image I noted that server returns a different image based on "User Agent".
The attacker can return the right file only if the system is x64 and is one of Linux distro reported above.
If it seems incredible take a look to the screenshot reported below. Request was made with Slackware distro.
Analyzing shellcode my attention was attract from string like the follow:
"4Ab9s1RRpueZN2XxTM3vDWEHcmsMoEMW3YYsbGUwQSrNDfgMKVV8GAofToNfyiBwocDYzwY5pjpsMB7MY8v4tkDU71oWpDC".
It is not a string base64 encrypted, what of it?
I retrieved a pastebin file where was present part of this shellcode, where I found the same strings.
As you can see, in this shellcode's snippet, if doesn't exist a file named "AnXqV" "Minerd CryptoCurrency" it is going to download and save into "tmp" folder with file named "AnXqV".
Then execution permission is assigned to this file.
At the end a command named "cryptonight" is running.
NOTE: CryptoNight is a proof-of-work algorithm. It is designed to miner bitcoin and to be suitable for ordinary PC CPUs.
According with handbooks every miner use a different command's format. In case reported above
command "-a cryptonight -o stratum+tcp://URL:PORT -u WALLET_ADDRESS -p x" is used to run miner. So, string "4Ab9s1RRpueZN2XxTM3vDWEHcmsMoEMW3YYsbGUwQSrNDfgMKVV8GAofToNfyiBwocDYzwY5pjpsMB7MY8v4tkDU71oWpDC" is a Monero's wallet address.
ELF file In-depth Analysis:
Analyzing ELF file I was able to retrieve more information about malware's type, its author and the URLs reached out.
Who create this software have nickname "fireice-uk", below there is a screenshot of his github's account.
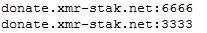
Also was possible to retrieve URL that are contacted by this miner
Checking domain owner, like in a fairy tail, website is liked to the Miner's developer (Fireice-UK)
Malware's developer embedded the miner developed by "fireice-uk". If the two person are different, why malware's developer have to use and include a miner developer my another person?
Below you can find evidence about matching between information extracted from ELF's file and source code created by "fireice-uk".
In my opinion who developed malware and miner could be the same person.